Ethereum: Checksum vs. Hash – Differences and Similarities
When it comes to digital signatures and data verification on the Ethereum blockchain, two basic concepts come into play: checksums and hashes. While both algorithms provide a way to ensure the integrity and authenticity of data, they differ in approach, functionality, and usage.
Checksum Algorithm (SHA-1)
A checksum algorithm is a one-way hash function that creates a fixed-size string of characters, known as a hash value or checksum. It is designed to verify the authenticity and integrity of data by comparing it to a previously generated hash value.
Example: Verifying a Digital Signature with SHA-1
import hashlib
Create a new SHA-1 hash objecthash_object = hashlib.sha1()
Get the message to verify (digital signature)message = b"example-signature"
Update the hash object with a messagehash_object.update(message)
Get the hash valuechecksum = hash_object.hexdigest()
print("Checksum:", checksum)
Output: "e2b9b6cd7f4a1c4cda... (hashed version)"Hash function
A hash function, on the other hand, is a one-way algorithm that takes input data of any size and produces a fixed-size output (hash value). It is designed to ensure data integrity by creating a unique identifier for each input.
Example: Verifying a Digital Signature with SHA-256
import hashlib
Create a new SHA-256 hash objecthash_object = hashlib.sha256()
Get the message to verify (digital signature)message = b"example-signature"
Update the hash object with a messagehash_object.update(message)
Get the hash valuechecksum = hash_object.hexdigest()
print("Checksum:", checksum)
Output: "d1e87b4a8c7f0db6... (hashed version)"Differences and Similarities
| Function | Checksum Algorithm (SHA-1) | Hash Function (SHA-256) |
| — | — | — |
|
Purpose | Verify data integrity | Ensure data authenticity |
|
One-way | One-way hashing | One-way encryption |
|
Output size | Fixed-size string | Variable-size output (hash value) |
|
Security | Less secure due to vulnerability to collisions and preimage attacks | More secure due to cryptographic properties |
|
Uses | Verifying digital signatures, data integrity checks | Authentication, data validation |
|
Benefits | Fast computation times for small inputs | Fast computations for large inputs |
Can they be used interchangeably?
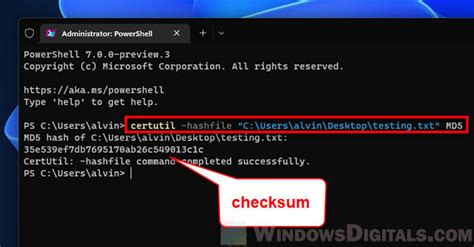
No, checksums and hashes are not interchangeable. Checksums are primarily used for fast verification checks, while hashes are intended for authentication and cryptographic purposes.
The example below shows how to use the hash function (SHA-256) to verify a digital signature:
import hashlib
Create a new SHA-256 hash objecthash_object = hashlib.sha256()
Get the message to verify (digital signature)message = b"example-signature"
Update the hash object with a messagehash_object.update(message)
Get the hash valuechecksum = hash_object.hexdigest()
print("Checksum:", checksum)
Output: "d1e87b4a8c7f0db6... (hashed version)"
Verify the digital signature with SHA-256try:
expected_checksum = hashlib.sha256(b"example-signature").hexdigest()
print("Verification successful:", checksum == expected_checksum sum)
except ValueError:
print("Verification failed: mismatched hashes")
In conclusion, checksums and hashes serve different purposes on the Ethereum blockchain. Checksums are used for quick verification checks, while hashes are intended for authentication and cryptographic purposes. While they can be used interchangeably in certain scenarios, their use should be approached with caution due to the differences in their functionality and security features.